Using LockMagic to provide 2 Factor Authenication
Using the LockMagic key Service, and Hotmail linked accounts, organizations can implement a form of 2 Factor Authentication (2FA) just using email addresses. Since Live Id supports registering any email address as an identity for authentication, organizations can link their corporate accounts with a Live Id. Thus, when an external sender emails a user in a corporation, double clicking on the message will force LockMagic to authenticate the user using the linked Live ID that was established. Since the corporate user has to sign on to the corporate lan using his corporate credentials, linked Live Ids gives an organization a second factor in order to authenticate the use. Even though corporate organizations have the ability to place a local LockMagic key Server in their organization, in some scenarios, this may not be an option if there is not another available resource to place the software on or for any other reason. With the external LockMagic Key Service and Live linked Ids, organizations will be able to send and receive encrypted emails.
Continuing, the same technique can be done manually for any user. LockMagic allows a user to send an email to one identity but have the contents of the email encrypted with the identity of another user. For instance, if a user has a live account and a Google account, it is entirely possible to send an email to this users hotmail account. However, the contents of this email will be encrypted such that user will have to authenticate to Gmail in order to view the contents of this email. Thus, even if one of your live email account was phished, the attacker would need to know the password of your Gmail account in order to actually read the contents of the email. Figure A, below, shows how LockMagic can be used to provide 2FA using email addresses.
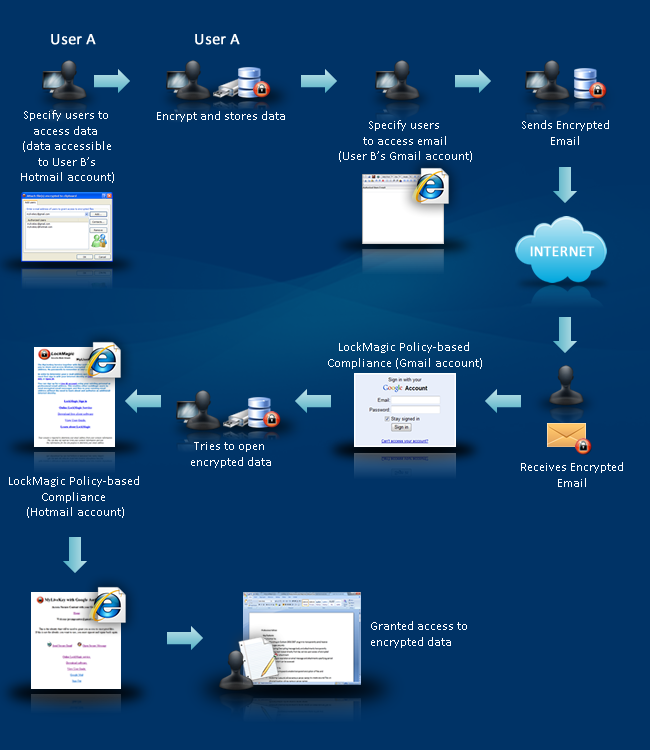
Fig. A
Lastly, using LockMagic, in combination with Open Id and phone authentication, gives the user another form of 2 Factor Authentication. With this combination, when a user tries to access encrypted content, a phone call can be generated to a predefined phone number to act as a second form of authentication. Figure B shows this scenario.
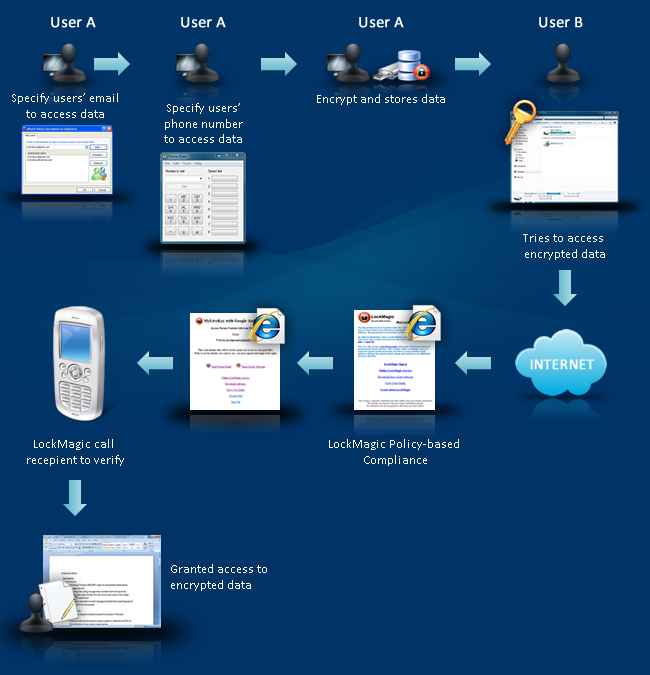
Fig. B
Highlights
- Provides 2 Factor Authentication with email addresses
- Provides 2 Factor Authentication via Google Authenticator or Yubikey